
System Security
Industrial-Strength System Security and Stability
Built on Trusted Technologies
Get all the tools necessary to make your system as secure as you need it to be. Ignition® is built on a solid, unified architecture and proven, industrial-grade security technology, which is why industrial organizations all over the world have been trusting the platform for years with their mission-critical systems.
Companies That Depend on Ignition:


Secure Communications
Ignition supports secure communication so you can seamlessly integrate your Ignition system with your existing security strategy. We know that your industrial data is vital to your business: that's why Ignition comes with the ability to safeguard your data with ultra-secure TLS 1.2 and 1.3 technologies. TLS is trusted by financial institutions all over the world to protect data and the communications channel it passes through.

Powerful Client Authentication
Ignition supports robust web-based authentication strategies, including federated identity, MFA, and SSO. The open platform enables you to centralize identity management with trusted technologies like SAML and OpenID Connect, integrate with corporate network security platforms like Microsoft Active Directory™, or manage roles and system access natively.
Keep Informed with Easy System Auditing
Ignition’s built-in user auditing gives administrators incredible insights about what is happening in the system, when and where it is happening, and who is doing what. This enables you to quickly resolve issues and mitigate costly downtime incidents.


Protect Your Data With Secrets Management
Add another layer of protection to your private data with Secrets Management, removing passwords, certificates, and encryption keys from gateway configuration.
Manage Security Settings
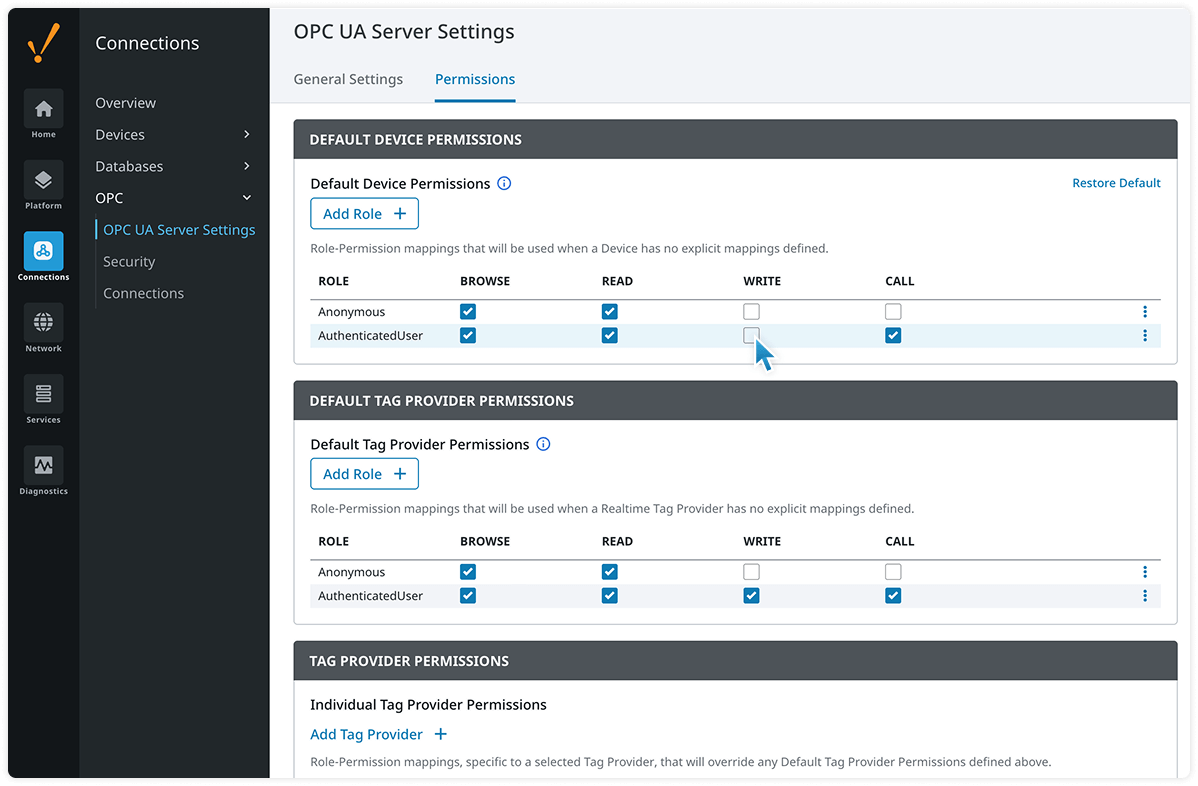
Ignition provides a wide degree of system control, putting you in the driver's seat of your security strategy. Use Ignition’s OPC UA Roles feature to pick and choose which operators, officers, and third-party users have access to specific devices or tag providers — and control the read and write permissions granted with that access.

Set Up Security by Location
Ignition's powerful security zones let you set up security rules based on location. Using security zones with user roles, you can control how and where a user can access the system, whether they are in a specific area on the plant floor or a remote site. Based on these zones, users can only access the system's functionality from assigned locations.

“With the Ignition SDK, we can put in our own protective measures and our own tracking. With our cloud server, we depend a lot on our firewalls and certificates. Ignition has played well with all of that with no problem.”
David Pitzer
Tyrion Integration Services

Security Starts Here
Trust in a product begins with trust in the company. Inductive Automation employs meticulous measures to ensure the safety and security of our entire infrastructure, from our facilities to our employees.
Visit our Security Portal
